Print | posted on Wednesday, April 04, 2007 9:26 PM
The SharePoint Configuration Wizard (and Central Admin) does a decent job of ensuring the neccessary privileges are applied to various users and resources, but one slipped through the 'net.
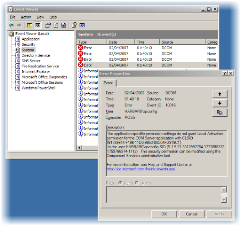 You know the one - it's that pesky DCOM 10016 which will fill up your System Log with noise everytime your application pool spins up.
You know the one - it's that pesky DCOM 10016 which will fill up your System Log with noise everytime your application pool spins up.
Now it just so happens that the error doesn't actually matter a stuff and won't break anything, other than your sysadmin's patience and respect for SharePoint! It's especially annoying if you are running Operations Manager or a Managed Security Auditing system which will bleet when this stuff gets logged.
So how to make it go away? Well it's easy you copy (without the braces) the GUID in the Description (remembering that the 'old' event viewer doesn't support context menus so use Ctrl-C) do a find in Regedit for the GUID and you'll get the name of the application for which access is denied.
It turns out you don't actually need to do that, because the GUID is a well known system component - the IWAM Reg Admin Service. So you need to fire up Component Services, right click on IWAM Reg Admin Service in DCOM Config and add your application pool identities to have Allow Local Activation. Just like Dustin blogged eons ago.
The trouble with this approach is that everytime you fire up a new web app in a new app pool the errors will unfold on you again. Of course generally it is a bad idea to add permissions to users anyway. What you need is a group into which all your app pool accounts get put, and then add that group using DCOM config. If you do that, 10016 will never again darken your days.
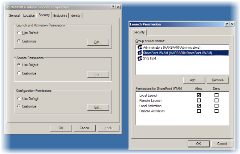 So you could create a group for that purpose, but why bother? There's one on your boxes allready, into which SharePoint sticks your app pool identities (as long as you use Central Admin to create them). It's called WSS_WPG. Sounds good right? No - because those groups are local groups - so not ideal good for a farm.
So you could create a group for that purpose, but why bother? There's one on your boxes allready, into which SharePoint sticks your app pool identities (as long as you use Central Admin to create them). It's called WSS_WPG. Sounds good right? No - because those groups are local groups - so not ideal good for a farm.
So the best current solution is to create a new Global Security group in AD (say 'SharePoint IWAM'), add your app pool identities into it and use Group Policy to fiddle with the DCOM Security. And remember don't give the group any more rights than it needs.